Making email secure again with PGP
Email is insecure by default. From its very first design in the 60’s, security was not a very big deal. Although nowadays it includes some security mechanisms, there is no end-to-end encryption solution built-in. In this post we will explain what is PGP and how you can use it.
Not bad: Pretty Good Privacy
In the 90’s some guy called Phil Zimmermann developed a new tool for email encryption. The software was named Pretty Good Privacy (PGP) and soon became the most used utility for protecting the confidentiality of the email.
Nowadays, OpenPGP is a a proposed standard of the IETF (see RFC 4880)) and there exist many implementations of it for email protection, available for the most used Operating Systems, including Linux, Windows and MacOS. You can check in the OpenPGP website the available software.
Asymmetric cryptography
I will not get into much detail about asymmetric cryptography here. However, it is very useful to understand the main idea behind the security of PGP. For this purpose, I will try to make a brief analogy for non-technical users:

Image: Ordinary mail is also insecure.
Imagine you want to send me some email so I am the only one able to read it. You may think it is a good idea to agree with me some password first, so you encrypt your text with it and then you send me the contents. Well, actually it is not a bad idea, but the problem is: how do we agree in the password?
If you send me first the password in another email, anyone could steal it and use it for decrypt the following message, so we need one way to agree this password. Here is where asymmetric cryptography comes in:
- I have a key pair: a public key (I can tell anyone) and a private key (I have it in my PC)
- You use my public key to encrypt the message.
- With some asymmetric cryptography magic, I use my private key to decrypt the message.
The security here relies in the fact that nobody is able to decrypt the message without the private key.
Web of Trust
Alright, I have to publish my public key somewhere and you have to trust that nobody has impersonated me and has put his public key instead of mine.
“Imagine” I have my public key in my website: https://martinord.eu/gpg. Somebody could intercept the communications or hack my website to substitute this file with their public key. Then, if you use this public key to encrypt the message you send to me, the attacker could read these contents and forward it to me. This is the well known Man-in-the-Middle (MitM) attack.
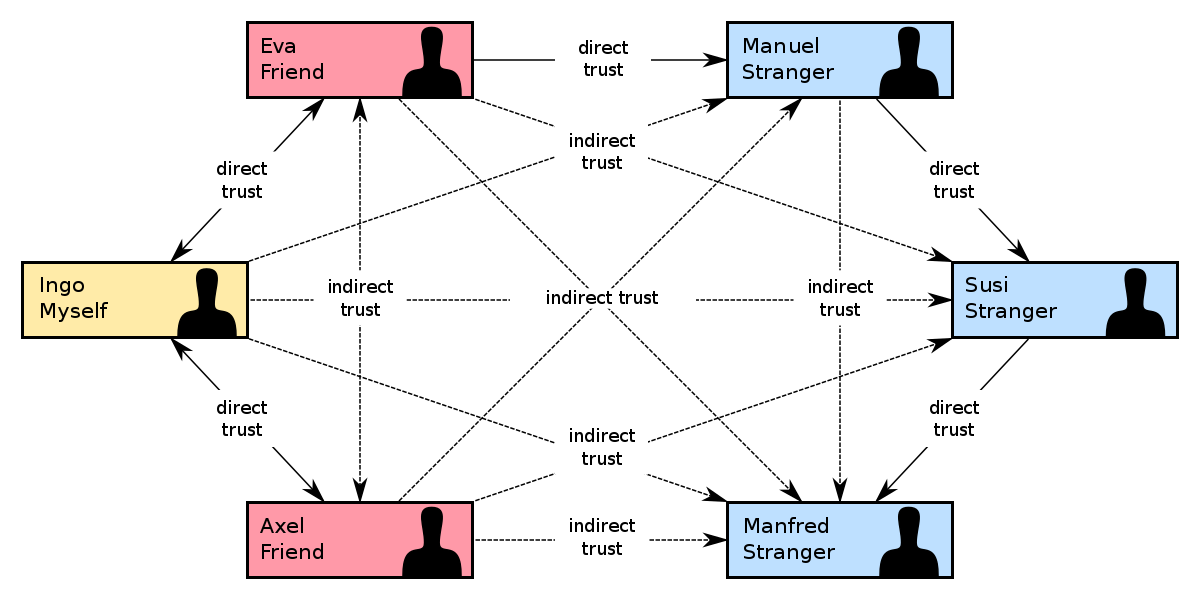
Image: Web of Trust (src: wikipedia.org).
To avoid this, Web of Trust (WOT) was invented. The main idea is to provide a decentralized way of trusting public keys of other people, without requiring a Certification Authority (CA) like in other protocols like TLS.
How does it work? Well, basically people can sign public keys from other people so, if you can really trust the key of John, then you will automatically trust a bit more the public keys that were signed with John’s public key.
Hands on: encrypt and sign your messages
So far so good, right? Well, let’s see an example of how to send and receive encrypted messages with OpenPGP and Thunderbird. This is compatible with Windows, Linux and MacOS, and does not require much configuration nor technical knowledge.
Thunderbird 78
Thunderbird is an email client that you can install in your computer. Basically, it is a program that allows you sending emails with (probably) any email account you have, including Gmail and Outlook.
The new version of Thunderbird includes a built-in feature for using OpenPGP with your email: https://www.thunderbird.net/en-US/download/.
In this article I will not cover how to setup your email account in Thunderbird, but it should be quite straight forward! After this, you can see the End-to-end-Encryption configuration by clicking on your account:
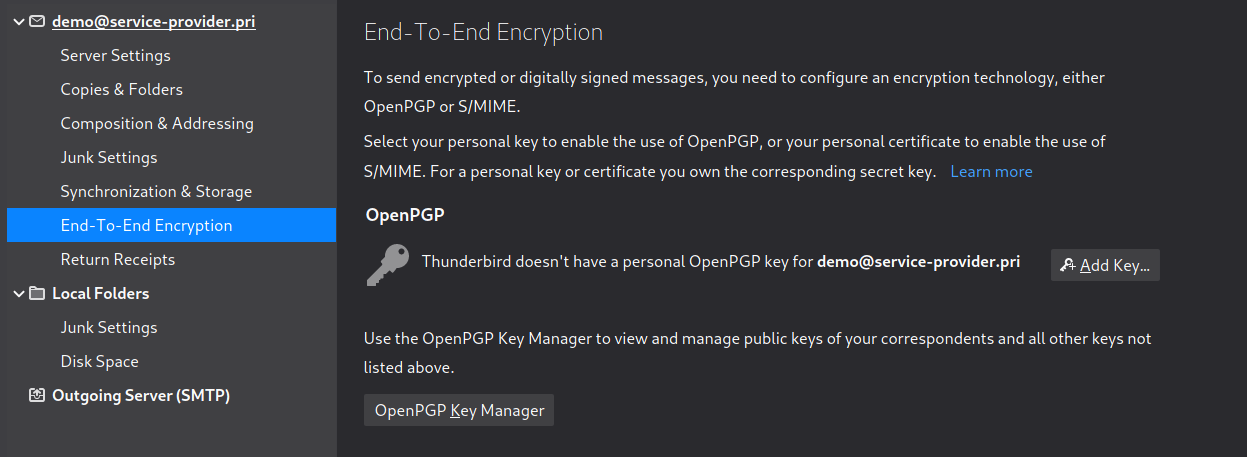
Your keypair
Once you have your account ready, you can generate your key pair:
- A private key for you to decrypt the messages sent to you.
- A public key for people to encrypt the messages before sending them to you.
This key pair can be generated by OpenPGP and being imported later, or you can directly generate them in Thunderbird:
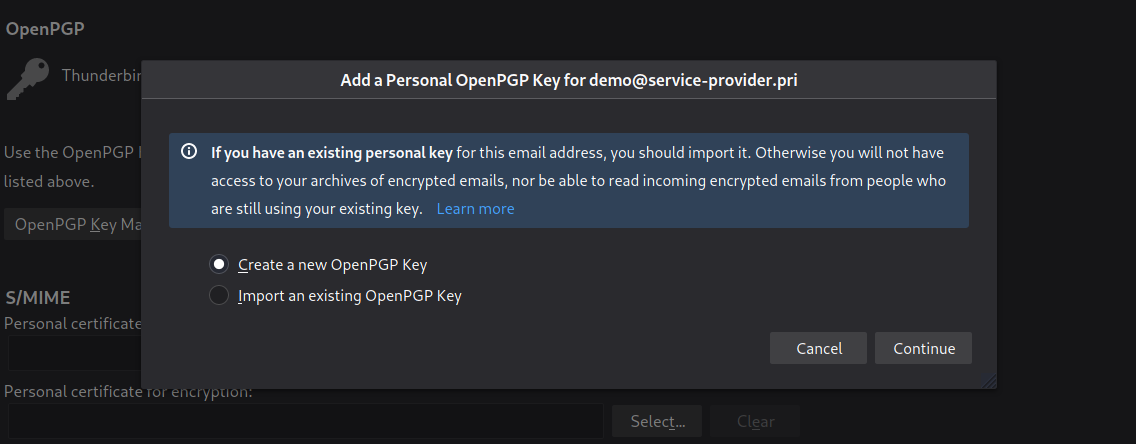
Keep in mind that you can also specify a key expiration time, so it will not be valid after this period. In this case, I have chosen 2 years for a ECC key of 4096 bits.
Now it is time to communicate securely!
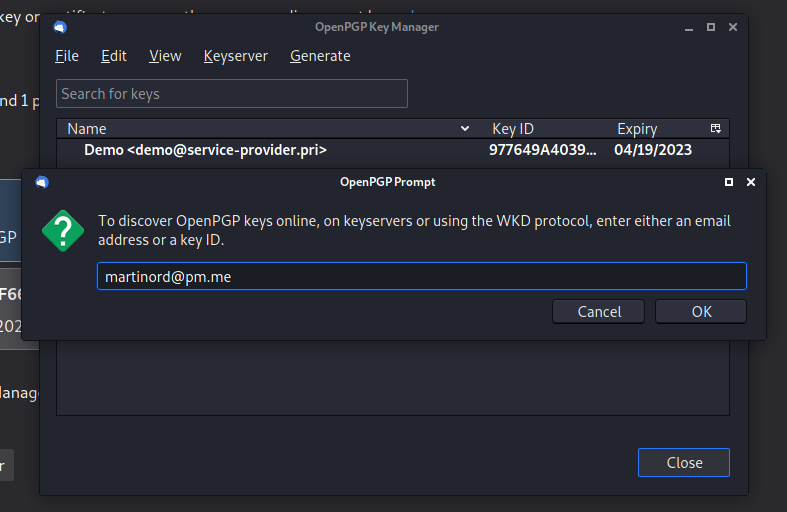
Now you have your keypair, you will try to send an encrypted email to someone else. For example, you cand send me an email! My public key can also be found in a keyserver, so you can directly import it from the OpenPGP Key Manager, under KeyServer:
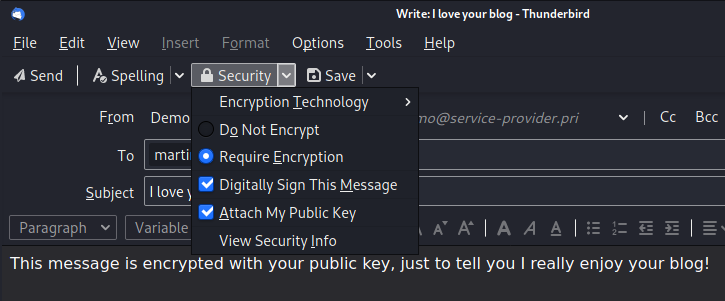
When composing a new message, you can see the Security options, where you can encrypt and sign the email. Keep in mind that you need the public key of the person you are sending the message to! Make sure also that you attach your public key so they are able to reply securely.
Conclusion
Email is insecure by default, although the new security measures like TLS and the later improvements in the protocols. However, in order to secure your messages protecting the confidentiality and integrity of your communications, you should rely on end-to-end encryption with asymmetric cryptography. Here is where PGP comes in.
With the new version of Thunderbird, they have incorporated built-in support for OpenPGP, which makes very easy getting, finally, in the pretty good private email again.
Obri! Hope you found it interesting and you start using it when you need it!